These Tools of Mine
Towards a New Design Ethic

True story:
More than twenty years ago, I was handed the opportunity of a lifetime. Or at least it felt that way at the time — I hadn’t lived all that long yet, after all.
I had been working the same menial job for about a year, doing physical labor for not much money. Enough to cover the bills and get blitzed at the local dive, but not enough to save for any kind of future, or to even pay the rent without tolerating a parade of increasingly psychotic roommates. I was adrift, in other words, as many men my age were (and as I suspect many more are now).
One day, a kind and brilliant friend of mine made me an offer. He’d recently begun working an IT job at a tech startup that was aggressively hiring, and he wanted to bring me on board. I was reluctant at first; what I knew about computers and IT could probably fit in one of those church pamphlets they hand out on street corners. The last thing I wanted was for my friend to vouch for me, and my poor performance to reflect badly on him. But for some unknown reason, he had faith that I would catch on quick.
This faith was sorely tested my very first day on the job. I was led into a cluttered alcove in the rear of the shop and introduced to the CEO — a huge, boisterous snake-charmer of a man in a pale gray suit. After some lightning fast small talk, this man pointed me to three objects on his desk: a Nokia cell, a Palm Pilot in its cradle and a Sony VAIO laptop. He said he needed to pop out for a lunch meeting, and in the meantime I should “Make these things talk to each other.”
I nodded firmly and said, “No problem,” as though I were a grizzled console jockey from Chiba City instead of a failed artist and professional wage slave. But I was quietly scared shitless.
My memory of the next few hours are a blur to me, all these years later. I remember the tactile sensations of flipping through paper manuals, and of sweat pooling in my pits and groin. I remember a lot of typing and mouse-clicking, but not what I typed or clicked. Mostly I remember the feeling of electrified panic; here was my very first test, and I was going to flunk it, big-time.
Miraculously, that turned out not to be true. By the time the boss came back, I had indeed made the little gadgets talk to each other, synching up their calendars and such. It turned out that I work very well under the gun. Who knew?
But the reason I recount this story is because of the gadgets themselves. The communications layer I rigged up was discrete, in the sense that its portable components (phone and organizer) synchronized directly with the laptop by wire. There were no external conduits or protocols involved. The bossman’s notes-and-scheduling toolkit was a closed system, protected by passwords that only he himself knew. If an individual component was lost or broken, he could buy a new one and restore the latest synced image from the others.
Offline gadgets like Palm Pilots and dumbphones seem almost ridiculous to us today; the goofy, nugatory artifacts of some cargo-cult past. After two decades of innovation driven by highspeed global communications networks, every gadget is merely a portal to a cloud, where the data we exchange is subject to all manner of surveillance, exploitation and theft. We price this vulnerability into an amorphous “cost of doing business these days.” Most of us can’t even imagine useful devices that function independently of ethereal networks, or free from the panopticon they represent.
The point of this article is that I think we should not only imagine them, but perhaps some of us should start to build them.
And sooner rather than later.
Here’s a thought experiment:
Imagine you live in a burning world. Not literally (in most cases), but in the sense that all institutional trust and value has been set ablaze, due to multiple generations of graft, incompetence and betrayal.
I know that’s a stretch, but give it a try.
This total institutional meltdown includes legacy financial and monetary systems, for whom the piper’s bill has finally come due. With the ink running dry on the money printers and nothing but gold and gas left to loot, global elites have now fully adopted their traditional roles as warring princes, deploying hordes of human and artificial assets onto an improvised neo-medieval battlefield of 5th Generation Warfare.
The human operatives of these new fiefdoms are mainly composed of amoral mercenaries and helots/neo-slaves; the former are paid in pirate fashion, the latter addicted to goods over which the prince and his corporate vassals retain monopolistic control. The artificial operatives are cloud-dwelling phantoms, with efficiency curves optimized for surveillance, logistics, propaganda, cyberwarfare and violent paramilitary action.
The lifeblood of such an enterprise is the uninterrupted packet flow of services and communications — with an emphasis on uninterrupted. In this environment, maintaining the illusion of godlike omnipotence will become critical to any regime’s survival. Those living under its spell will seem not quite human to the rest of us, driven to unplumbed depths of Lovecraftian madness by the constant flow of ads, meds, games and porn. The seemingly all-knowing and seeing Eye that supervises this flow will be internalized at the level of metaphysics for them, rendered as impossible to resist as the will of God.
Practically speaking, the flow will continue to afford the new regimes many of the same advantages we see today: cutting edge computational services that are widely distributed across a global communications grid, and boasting nigh-instantaneous synchronization and nigh-immortal redundancy. But in order to reliably deliver these services, a physical network must be maintained. This capital-N Network forms the backbone of everything you see on a screen today, located at data centers, server farms, telecom junctions and other infrastructural nodes.
In the proposed fiefdom model, the physical Network is populated by small-n ethereal networks whose borders most be ruthlessly sealed and policed. Arguably this describes our current situation too, but with a somewhat milder interpretation of “ruthlessly.” In the new model, where deepfakes and soup-pots have killed off dinosaurs like The News™ and transformed government into a something more akin to an evil imperial church, any given battlefield can turn kinetic on a dime, and without even the pretense of accountability. A drone swarm razes a village in the dead of night, twenty miles east of where you sleep. You awake to crickets (and perhaps to a breakfast of cricket-burgers).
Most won’t know or even care to know what’s happening in the larger world, because to try to do so would be as ridiculous as trying to outwit a tornado. The regime’s packet flow of propaganda is all you have to go by anyway. And so long as it also keeps feeding you games and porn, pills and potions, high fructose and cheap proteins, you will “believe” whatever it tells you to, and do exactly as it commands. That’s because while these various neo-medieval fiefdoms will differ in certain aesthetics, all will include the same Black Rule at their core:
All is given.
Thus all may be taken away.
A real black-pill downer, right? Yet I think it’s safe to say that this reality, or something very much like it, is coming soon to a theater near you.
But there’s a catch. Several catches, in fact.
The first is this: not everyone will live inside such a nightmare, voluntarily or otherwise. There will be pockets of resistance, unconquered tribes, roving bands, lordless knights and samurai, who live and thrive along the fractures and fringes between kingdoms. The human being is defiantly creative, intelligent and adaptable, and many of us are rendered impossible to rule as a result.
That’s not to say the bastards won’t try. The bottomless appetites of their egregores and demon-gods will demand we be found and brought to heel, subjected to public humiliation, suffering and even execution. To them, we’d serve as the perfect attraction in their new bread-and-circuses model, both as dark amusements and as cautionary tales for those who entertain thoughts of jumping ship.
But the other catch has to do with something some old, dead Chinese guy once observed about asymmetric war:
“Let your plans be dark and impenetrable as night, and when you move, fall like a thunderbolt.”
— Sun Tzu
Perhaps you’re thinking this refers to off-grid living, in our scenario. Yes, but that’s only part of it. The Amish can be as “dark and impenetrable” as they want, but they sure as hell ain’t falling like thunderbolts. That requires an arsenal of strong and reliable tools which are easily wielded, and with minimal training.
Besides, my goal in this thought experiment isn’t to be Amish, anyway. My goal is ultimately to win. But in order to survive long enough to win, we must be able to live as well and freely as possible, which will include the use of certain technologies to our advantage.
To achieve this, we need to reimagine the current design standards for our tools. We should start looking at the current state of digital networking technology as if it’s merely an interim step towards what will become a radically different evolutionary path, rather than a telic death march unto Borg-like totalitarianism, menticide and slavery.
Like all design standards, there will be tradeoffs. For example, our new tools will lack many of the strengths of those developed in accordance with the pure Network standard, but will likewise circumvent many of their weaknesses.
It won’t be easy. A lot of the early work will involve repurposing older tools, or using existing infrastructure in new ways. Lucky for us, artists have already supplied some very useful models to draw from, and in the not so distant past.
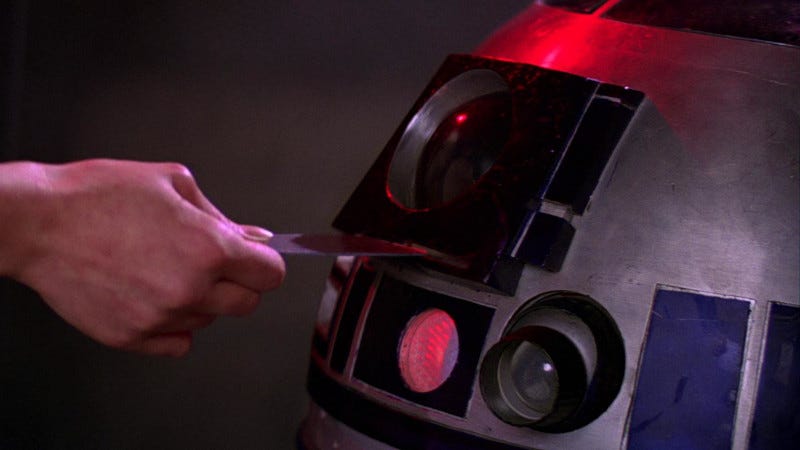
To say Rogue One: A Star Wars Story is a bad film is an understatement, in my opinion. I won’t get into all of my reasons for disliking it, of which there are many1. For the purposes of this post, I just want to focus on one aspect of the plot: remote communication as a storytelling element.
One criticism I’ve often heard about Star Wars as a fictional universe has to do with precisely this element. People in these films appear to communicate and transmit data in ways that magically expand and contract from scene-to-scene, depending on the current dramatic need. Basically, the notion that these folks can hop around the galaxy at light speed but have yet to master email tends to antagonize fans of harder science fiction.
And while stashing the Death Star plans in an animatronic trashcan may work for comic relief, it looks altogether absurd amidst all the other hi-tech stuff we see. But in its clumsy attempt to repair the problem, Rogue One succeeded in only making it worse. By the film’s end, we are living in a wacky dimension in which massive data centers and dish arrays are required to beam a set of blueprints to a spaceship, where they are then compressed onto a tiny data-wafer that can be hidden inside a small robot. The newer film therefore makes a further hash out of a story beat that was already nonsensical, while adding nothing of value to the drama or plot.
And yet, it recently occurred to me that there’s something useful buried within the concept.
Whenever I read a book or watch a film that’s trying to establish a believable fictional world, I only ask that this world make minimal sense on its own terms. I’m fine with elements of sorcery and far-fetched tech, so long as they conform to a set of rules that are consistently applied. So when I watch films like Star Wars, I will compensate for the often extreme gaps in logic by filling them with my own explanations.
In the case of Star Wars, I can sum up my repair efforts as follows:
The Galactic Empire is the apotheosis of a powerful Network-based regime that conquered and incorporated all rival fiefdoms. Their communications technology can be seen as an inflection point along our current curve. It is long-distance, pseudo-instantaneous, ethereal and bidirectional, exploiting all the recognizable strengths of the Network communications model to organize, command, decieve and surveil.
The only components of the Rebel Alliance who participate in the Network flow as intended are spies like Princess Leia. Posing as ambassadors and imperial functionaries, they keep an eye on the packet flow for any information that could potentially damage the regime.
Because the Network infrastructure and its subsystems are controlled by the regime, such spy data cannot be securely transmitted along the flow. Therefore it must be transferred onto discrete physical mediums (e.g. the Bradley Manning model) and handed directly to trusted agents in person.
The same holds true for the Rebels’ dodgy, inconsistent use of ground level and ship-to-ship communications. Because the newer, robust and more advanced tech the Empire employs is inherently untrusted and non-secure, they must resort to using older, clunkier and less powerful means of communications and transmissions in order to stay off the enemy’s radar, so to speak.
These explanations are imperfect (and certainly can’t repair all the retconned absurdities of the execrable new Disney products). However, I think they’re plausible enough in terms of how asymmetric warfare might actually be conducted, in the near future I described above.
The design tradeoff here requires sacrifices of liberty for security2, with "liberty" here referring not to human freedom, but to the speed, ease, reach, affordability and utility of the enemy's networks (i.e. making "liberal use" of something). While that might sound a bit strange given what it is we're fighting back against, in this case the enhanced security mainly comes in the form of enhanced proprietorship at the cost of weaker or more restrictive use.
For instance, you do not “own” your smartphone in the same way you might own a record collection, or the clothes on your back. Rather, the aspects of your phone that you do own3 are vastly outweighed by those you don’t. It would be akin to owning every part of your bicycle except the wheels, which Big Wheel can legally strip you of at any moment.
The strength of using such unowned tools has been obvious. As programmers, for example, we can collaborate on very complex problems and projects at great distance. As artists and authors, we can attempt to explore truths, convey meaning and forge a connective tissue of trust that extends around the globe. We can learn new skills, and even entire trades, for free in our spare time, and engage in business at a global level. In fact, it’s difficult to imagine any human enterprise that hasn’t been greatly advantaged by the rise of hi-speed digital networks.
For some of us, the drawbacks are equally obvious. By using the enemy’s tools, we are forced in many ways to play by the enemy’s rules, and therefore become subject to its many whims and appetites. If the Trump and Covid years have revealed anything, it’s that the forces of globalism and their puppet governments will flex their barely concealed muscles unabashedly, the moment the situation demands it. CBDC, ESG and illegal WHO treaties will mark the next big flex, but certainly not the last.
In light of these strengths and weaknesses, the question becomes something like this:
How can we leverage current (or very recently deprecated) technologies in such a way that our tool evolution prioritizes ownership, independence, privacy and portability over the regime-dependent model?
I don’t have the anything like a complete answer at the moment. But I am starting to examine the question itself in greater depth, with an eye towards current and future development of technologies that are both highly personalized and freedom-oriented. Some of these tools and software packages will be specifically defensive in nature, while others will be be life-enhancing in the sense that they provide secure workarounds for all the everyday Network transactions we take for granted. They will even include tech that will help us build and manage parallel societies of free peoples, or rebuild the current version when it inevitably collapses.
What follows is a (brief, non-exhaustive) list of general design principles in that direction, submitted for group analysis and debate.
1. Proprietorship
All devices are wholly owned by their users, including any and all physical components, media and data stores. In the case of digital applications, all software is open source and fully accessible/customizable by the device’s owner. Transfer of ownership is direct in both its physical (handing the device to its new user) and digital (changing of passwords, managed rights, etc) components, and involves no third-party transactions or agreements. New software-driven releases transmitted across wired or unwired networks must be rendered fully transparent, easily rolled-back and subject to personal approval by an individual device’s owner prior to install.
2. Security
In its default state, a device capable of bi-directional Network communication deploys a combination of cryptography, tunneling and blockchain transactions to ensure the user’s privacy. It lacks the hardware/software required for audiovisual capture, and incorporates Faraday-shielding into its design implementation.
3. Portability
The device is designed to be a) carried or worn on your person or b) suitable for easy transport by private vehicle. Wearable devices conform to a sturdy, lightweight ergonomic design that maximizes mobility and leaves hands and feet unencumbered when not in use (e.g. holsters, headgear, backpacks, vambraces, greaves, bandoliers, etc).
4. Recyclability
The device favors the repurposing of deprecated or “obsolete” hardware as the components and/or base platform for new designs, leveraging the low cost, legality of ownership, ease of modification and stronger security profile of legacy devices that were in wide usage a decade (or longer) ago.
5. Offline Functionality
The device possesses (or can possess) at least one inherent utility (or bundle of utilities) that operates completely independent of the Network, its service providers and their various seen and unseen masters. Such utilities may include sensory enhancement, survival multiplication, threat identification tools, defensive countermeasures and more.
6. Modularity
The device favors an architecture of modular, hot-swappable components, each of which can be repaired, replaced, modified or otherwise serviced independently of its original manufacturer(s) and designer(s). If the device is media-driven, this could include swapping out entire operating systems with minimal effort, effectively transforming one device into another (e.g. the same hardware used for live language translation could be turned into a blockchain trading tool by switching out a single component).
7. Durability
The device should be housed and/or externally protected such that it can survive most inclement weather events, camping, wilderness travel and general rough-and-tumble use.
8. Wieldiness
The user should not require expertise to properly wield the device as intended. The design ethic therefore favors straightforward implementations over advanced features (see below). However, advanced options and customization are always available to the more demanding user, whose needs and know-how may grow over time.
9. Acuminated Development
The device’s initial engineering and all future upgrades are focused on building, maintaining and honing core functions rather than provisioning for future features and expansions (e.g. the sword becomes sharper and/or sturdier, but does not evolve attachments for umbrellas and keychains). Furthermore, the honing of a given function is guided by all other design standards.
10. Cost-Effectiveness
The design for any given device should favor most-bang for the fewest-bucks. While this may seem obvious, the Network/cloud-based developmental model has shown a tendency for bloat, feature-creep and other artifacts that distort the cost-efficiency curve. New designs should never seek to reinvent the wheel, and upgrades should be restricted to the bare minimum required to improve core functions and/or security.
This list isn’t meant to be exhaustive. In fact, I think it can be improved in many ways. It’s really meant as a starting point of a conversation, for those of us who prefer to use our gadgetry rather than be ruled through it. I encourage others in our circles to add their ideas, insights and concerns.
In the meantime I plan to propose examples in the coming weeks of various devices that could potentially be designed in accordance with this ethic (or with something like it). That’s not to say they’re all feasible, or even to promote them as the springboards for physical projects at all. The main point behind these thought experiments will be to demonstrate how the future of tech isn’t the cattle-chute-to-slavery many of us have been tricked into believing. It’s filled with possibilities for technologies that actually free us from the grasping fingers of tyrants, and function to protect that freedom for ourselves and each other in the long run.
Looking forward to your comments.
(But no fedpoasts)
P.S. If you found any of this valuable (and can spare any change), consider dropping a tip in the cup for ya boy. I’ll try to figure out something I can give you back. Thanks in advance.
Although, if I ever decide to move forward with my “Movie Garage” concept here at Substack, my wife convinced me I should use Rogue One for my pilot episode, as she really likes the fixes I proposed.
Ironically, as the sacrifice is made to further the wider cause of human liberty.
And even there, you’ll find you don’t truly own those either, if you’re the type who dutifully reads your EULAs.





Brilliant article, Mark. I really like the direction of this. I've been playing with a concept I call slow-tech as opposed to low-tech. It doesn't require or provide 24/7 connectivity and maybe is completely non-commercial. It's hard-wired, maybe only with neighborhood hubs. Once a day, people may see who's responded or write/ read other posts. But the rest of the time, we're with the real people in our lives.
In everything, I see the resistance happening by communities taking back their power. I think about how Julian Assange was able to get around the censorship because little Iceland was a safe haven for internet freedom. If there's even one community that's publishing the truth, it makes it accessible to everyone.
I also think that taking back something as slow-tech as local radio, networked into independent producers everywhere, could be community-building.
You've given me a lot of food for thought, and it sounds like you'll be continuing to. Thanks for abetting my practical, post-apocalyptic dreaming!
This is really not my area of expertise, but I certainly have long imagined the utility of a word processor and printer that cannot connect to wifi.