A couple of weeks back, I had an animated conversation with Dame Bisone. It began with boobytrapped steampunk gizmos and caveat emptor, and ended in the realm of deindustrialization, captured supply chains, disaster capitalism, strategic chaos, mass human sacrifice, and the technosatanic plot for world domination.
That’s a familiar trajectory for many of our conversations these days, whenever Something Happens.
In this case, the Something that Happened came in the form of a remote grenade attack. This action was asymmetric, included psywar elements, and triggered a number of downstream effects that are diificult to measure. It therefore also qualified as a magical attack, by my own definition.
The day after the walkie-talkie sequel op, an old pen pal reached out to me. He figured I might be in a very bad mood. Not because of any political sympathies I hold for Hezabollah, or even due to the depravity of the attacks and their civilian casualties (although these latter two aspects have weighed heavily on my mind). He instead recalled how a decade-younger version of me used to rant and rave about pagers being “the wave of the future.”
A dystopian future, to be sure. A nightmare planet where cyberspooks, digimoles, and microassassins haunted every millimeter of PCB wafer and transmission line. Haunted people, too, thanks to the anti-sacraments of brain implants, genetic manipulation and other Frankenstein tech. In my mind’s eye, this future was a retort to Gibson’s anarcho-capitalism, with all the punk rock romance squeezed out.
All the nonsense, too. There were no console cowboys “jackin’ in” to do battle with Black ICE genies. In this world of mine, plugging anything into your body is a game of Russian roulette with six bullets, and the best possible outcome was turning yourself into a humanoid hand grenade for Globocap.
In fact, all devices connected to The Network in that fictional world were deemed haram, because to use one is to be seen, heard, and potentially touched by its distant masters.
In response, the heroes must bite the proverbial bullet, and degrade their tools. They become junk dealers and dumpster divers, sifting through the scrapyards of obsoleted products and methods to reanimate. As prisoners of a panoptical Mordor, ingenuity is the key to surviving with your soul intact. As rebels, the only way to effectively fight back is evading the Eye of Sauron at all costs. To appear on its radar was to summon a swarm of autonomous H/K ringwraiths, with predictably swift and grisly results.
So, in the world of this fictional story, the seemingly logical solution was pagers.
Not just those, mind you; what I imagined was an alternative communications eidos, with a grid cobbled together from re-provisioned and modded-up zombie-tech. Blackberries, palm pilots, walkie-talkies, hams, shortwaves, RC toys, magnetic tape, birdcalls, bike couriers, fireworks, airhorns, programmable Christmas light displays, carrier pigeons and more. All physical components were flexible, contingent, and subject to local adaptation. At one point in the story, two rebels try to decipher a message from the timed release of colorful birthday balloons.
What I’m saying is there were many tools and methods that constituted this imaginary comms architecture. But the pager — a low-band frequency-hopping receiver, routed through encryption gateways — was part of the standard issue loadout for a rebel operative, and was in many ways iconic of the rebellion itself. If it ever got made into a movie, I assumed this device would feature heavily in the marketing.
I’ve never published any part of this story or its speculative communications model, here on Substack or anywhere else (the closest I came was to muse about what a design ethic for free peoples might look like).
But over the years, I continued to think of encrypted pager networks as a viable option for small-n parallel networks. In terms of degraded capabilities versus improved security, you got the most bang for your buck. Hell, Twitter seemed almost like a training module for how to use their modest messaging capacity effectively.
Some likeminded friends thought this solution was too unwieldy and extreme, and even blackpilled to the point of surrender. I was told that p2p tunneling with quantum encryption would save us from such a sad caveman’s fate. And by “us” they meant people who creatively utilized The Network’s resources at depth and scale. In cutting off the spigot for non-regime aligned techies, the “rebels” would lose access to some of the most valuable human capital on the battlefield.
I don’t think that’s overstating it; the kind of people who can design, program, implement, and maintain the code that runs your data-transaction hardware are essentially the wizards and warlocks of our age. But without The Network’s backbone to support their magic, their wands would become firewood and their scrying stones paperweights. Development may continue in the boutique sense, but the freedom and bandwidth required to push out heavy packages and run realtime apps would be limited to whatever a hacker could manage without risking fatal exposure. In that sense, ceding that terrain to the Enemy sounds like throwing out ten babies with a drop of bathwater.
And the disadvantage doesn’t end with neutered tech wizards. By “The Network”, I don’t only mean the all those NAC nodes, data centers, towers, satellites, and endless sprawls of underground cobwebs. It also encompasses the entire noetic and physical infrastructure of the global manufacturing and supply chain. It’s the same invisible, ineffable chain that delivers all the other complex goods, right down to the one in your hand.
Now, hold that little black mirror against your ear, next to your beloved face and eyes and brain.
Is it ticking?
More to the point: would you even know if it was?
The Pocket Agent
I don’t say any of this to scare you. If you trust my insights or instincts about technology at all, I can confidently say that your smartphone is almost certainly not rigged to blow.
It is, however, almost certainly rigged to spy.
Most of you probably already recognize the truth of that, if only in some blurry way. Your every transaction is being tracked, weighed, itemized, scrutinized, and sold along multiple vectors. We don’t engage across this spy market because we’re particularly brave or stupid. We do it because it’s the cost of doing business in our Magic Bean Economy.
We are the Jacks in this economic model, who trade our fiat-currency cattle for the ensorcelled beans. The key difference is that we don’t buy our beans on faith alone; we see plenty of magic beanstalks towering all around us, and with ever more amazing phaseolus vulgaric upgrades constantly advertised. Taller stalks! Cooler castles! Fatter geese, laying bigger golden eggs!
As for those gigantic cannibals who guard them?
“Never fear,” says the sorcerers’ marketing and PR teams.
We have ways of dealing with them. We have Okta and Progress and CrowdCloudStrike. So don’t worry your pretty little heads about those Fee-Fi-Fo-Fucks.
Don’t ask questions. Just trust us, man. We got this, bro.
It’s not so easy to pick out the school of sorcery most responsible for the spaghetti mess we’re in. Catastrophic cybersecurity failures and our current state of patch-and-push enterprise software development go hand in hand. Even if we could trust the security guards (Spoilers: We can’t), the latter has devolved into a fat, lax, slovenly, naked and supine whore — and one which is compromised by thieves, saboteurs and spies at each and every organizational rung, by the way.
As Deimos technology officer Fukitol put it in a recent comment (emphasis mine):
Re: software, every day I am more convinced that any program too big to be comprehended, let alone written by, a single person, is one too dangerous to exist. I joke somewhat, but trying to understand what's wrong in an interaction with an API with the surface area of the Sun is a mortal infohazard. As I'm lately rediscovering. Small programs that do one thing and do it well, maintained by one individual, is The Way, and things the scale of Windows, let alone AWS, are the devil incarnate.
I've been on a continuing project of replacing colossal bloatwares with small programs written by me and tailored to my specific use case for a few years now and the sanity levels of my computer interactions are improving therewith. For people who can't or won't do this I recommend judicious application of a hammer, and thereafter touching grass (but be sure to remove the battery before you smash it - funny how they've made that task needlessly complex lately)
What does he mean by that last part?
He means that if you’re the kind of user who can’t be bothered to understand what kind of transactional sorcery you’re dealing with, or recognize the tradeoffs you’re making, you might as well be holding a bomb in your hands. This has implications for geopolitics and war, because most-or-all of the empowered decisionmakers fall into that latter “can’t be bothered” group of know-nothings.
This quickly became obvious in all the officially non-official commentary about the Lebanon attacks. It might seem passing strange to many filthy casuals lay observers that a market for pagers would exist at all in 2024. But when you understand their premium service offering and clientele these days, that picture becomes much clearer.
It’s the same reason, for example, that former Secretary of State Hilary Clinton’s staff were issued Blackberries instead of iPhones. Smashing those Blackberries to death with hammers is of course exactly what Hilary Clinton’s staff did, upon completion of their run at the State Department. In that case, it wasn’t because they were too incompetent to use them safely — they were, but that wasn’t the operative reason.
Earlier this year, Nasrallah himself explained the reason succinctly:
“You ask me where is the agent,” Mr. Nasrallah told his followers in a publicly televised address in February. “I tell you that the phone in your hands, in your wife’s hands, and in your children’s hands is the agent.”
While they were talking about two different kinds of security, both Team Clinton and Team Nasrallah understood that the bleeding edge of technology cut both ways. They were therefore willing to take the hit on functionality in order to secure their operations against death, whether by the slow hand of criminal justice (Clinton) or the lightning rod of asymmetric war (Nasrallah).
They both made mistakes. So far, only one party has suffered the consequences, because he misjudged The Network’s actual size and scope. So, in trying to evade one form of witchcraft, he plunged his guerilla army headfirst into the cauldron.
Before we continue, let’s get this out of the way:
It is true — or true enough — that pagers constitute an inherently more secure communications medium than cellular phones, due to the receiver-only design of the former. Without the ability to emit, you can’t geolocate the device by signal.
Modern pagers are even more secure than their ancestors, employing display locks, AES-128 encryption algorithms, and even remote “button touch” deletion of all stored keys and messaging data. That aside, you’re basically just looking at a fancier version of the gadget your doctors and drug dealers used in 80’s and 90’s. It does basically the same thing, but with greater capacities for receiving, storing, organizing, and loading data.
The AR-924 uses the POCSAG protocol for messaging. While obviously deprecated from the standpoint of modern cellular networks, POCSAG has remained the standard for many emergency services due to its reliability and coverage. Because pagers receive signals on low frequency bands, the networks can penetrate the concrete and steel of densely packed urban environments, and also cover remote rural areas that would be “dead zones” for cellular clients. That’s why pager networks operating on this protocol (or Motorola’s similar FLEX protocol) continue to be used at least as a fallback option for firefighters, medics, police units, and other emergency personnel (not to mention some more interesting clients, as we shall see).
While POCSAG/FLEX itself doesn't natively support encryption, messages can be encrypted before they are sent using application-level encryption. This ensures that even if the data is intercepted, it can’t be read without a decryption key. Routing POCSAG/FLEX messages through secure gateways that encrypt and decrypt the messages adds an extra layer of security. Such gateways can be integrated into an existing infrastructure at relatively low cost and effort.
So, what I’m saying is that Hezbollah’s plan wasn’t necessarily idiotic or insane. With a well-planned and competent rollout of current-gen pagers, the move might have worked out for them more or less the way they imagined it, confounding efforts to geolocate, intercept or surveil while not significantly downgrading the C&C structure. As mentioned, I myself have made arguments for re-provisioning deprecated tech. It’s not crazy in theory — and could in fact be crazy-like-a-fox, if you do it right.
Hezbollah most certainly did not do it right. In fact, they fucked up royally.
But the main point here is there’s nothing special about the “tech” itself. Pagers are old hat, yesterday’s news, been-there-done-that. Same goes for the way it was weaponized; at the risk of sounding cliché, remote-triggering a bomb with a phone call or RF transmission ain’t exactly rocket science.
While some excitable feline commenters leaped straight into the realm of… uh… hemianopic in-fur-ence, the above diagram is the most likely scenario for our pager IED, or for any other open receiver-based attack. The firmware is tweaked in such a way that the microcontroller will send an electric pulse to detonate the explosive (PETN, probably). The battery compartment is just a guess for where the fissile material/detonator would be secured. You wouldn’t want it placed on anything detachable (i.e. the battery itself), since that would increase the chances of discovery or disarmament. Reprogramming the firmware would require the most “technical” sophistication here. But considering the vast attack surfaces and sloppy dev-cycle that Fukitol described, we aren’t talking about a moon shot there either.
So when all the palace guard newscritters gush about the “ingeniousness” and “sophistication” of the pager op, they hopefully aren’t referring to the attack method itself. What they’re referring to — again, hopefully, because they ain’t rocket scientists — is the tradecraft and logistical sorcery that made it possible.
To wit: How did the attacker slip its agents into both Hezbollah’s purchasing process and the global supply chain, without raising any flags or leaving any fingerprints?
The question is far more complex and important than it seems at first blush. Sorcery of this kind is about as close as you’ll get to a One Ring form of power in our current industrial environment. Not only is the source of this power completely invisible to the consumer base, but it might even be misunderstood by those spooks and other shady supplicants who retain its services.
If you recall Elon Musk’s AI analogy about “summoning the demon,” you might get a sense of the path we’re on. Except instead of artificial general intelligence, what we’re talking about is a mirror maze of paperless transactions, phantom agreements, straw purchasers, and transnational Potemkin companies that disintegrate on command. So while the exploding pagers were the visible tip of the spear, the reputational damage done to the vertically integrated global supply chain itself was much deeper, and could prove far deadlier if the mystery is left unsolved.
By that I don’t mean the mystery of Whodunnit. Whoever the culprits were in this particular war crime1, it won’t be the last time we see this tactic rear its ugly head. When we analyze it in comparison with all tactics that came before it, it doesn’t just stand out as yet another escalation, but as an existentially dangerous one that only a madman would dare commit himself to it. In doing so, another djinn has been freed from its bottle, another seal irreparably smashed. Pick your apocalyptic metaphor, because it’s exactly that bad.
Or it could be that bad, in any case. The only way to prevent this spell from spiraling into World War III is to reverse engineer the magic, and expose its shadowy magicians to the light of day. With that in mind the most important mysteries to solve become Howdunnit and Whendunnit.
The Golden Thread
Somewhere in the ether, there exists a full transaction history for the pager attack: an ordered sequence of email threads, phone logs, order forms, receipt slips, shipping manifests, customs documents, inspection seals, security footage, and other records that would connect the initial seed of the plan to the ultimate explosion.
Our problem is that the public version of these transactions only shows us a select few of these nodes, scattered up and down the chain. This might be the case even if we had a trustworthy press full of investigative journalists, instead of our current batch of regime stooges and stenographers. That’s because the intel agencies aren’t the only obstacle here; even standard corporate policies and privacy laws would make it difficult, time-consuming, and expensive to fully reconstruct the trail.
But because the Blob exists, some of these nodes are at the very least questionable. Some might be even red herrings designed to throw various governments and agencies off the trail. So typically, the way we receive our information about events like the pager/walkie attacks follows roughly the same pattern.
First, wire service stringers report the raw data (multiple simultaneous explosions, blood and chaos, overwhelmed emergency services, etc), establishing that Something Happened at a particular time and place. The raw information isn’t always immaculate, and may be subject to rounds of digital fuckery, misreported numbers and other editorial funny business. But in most cases, the event is given sufficient coverage to mark as minimally credible.
Next, a bunch of nameless, faceless storytellers are cited by The Washington Post, The Wall Street Journal, The New York Times and other American birdcage liners, all of whom have great incentive to keep their sources happy by retailing their version of the event for general audiences. The same goes for their counterparts throughout Europe, Asia, MENA and beyond, who also tend to cite invisible men. They are typically referred to by pseudonyms, such as “a source close to the investigation”, “an official who preferred to remain anonymous”, “unnamed intelligence and defense sources" and so forth.
These nameless confidantes are by their very nature untrustworthy narrators, and their tales should be taken with several truckloads of salt. That said, the best red herring (like the best propaganda) will embed elements of verifiable truth in order to better deceive its target(s). That might even be the case if the “verifiable truth” is an encoded message or symbol, intended for a esoteric audience.
So, let’s begin by reviewing the transaction history evidence that’s been cleared for peasant consumption, and see if we can squeeze any truth from it. To do so, the wife and I donned our hazmat suits and waded into the sludge of all the regime-approved “clues”, as regurgitated by their A-tier propaganda outlets. You’re welcome.
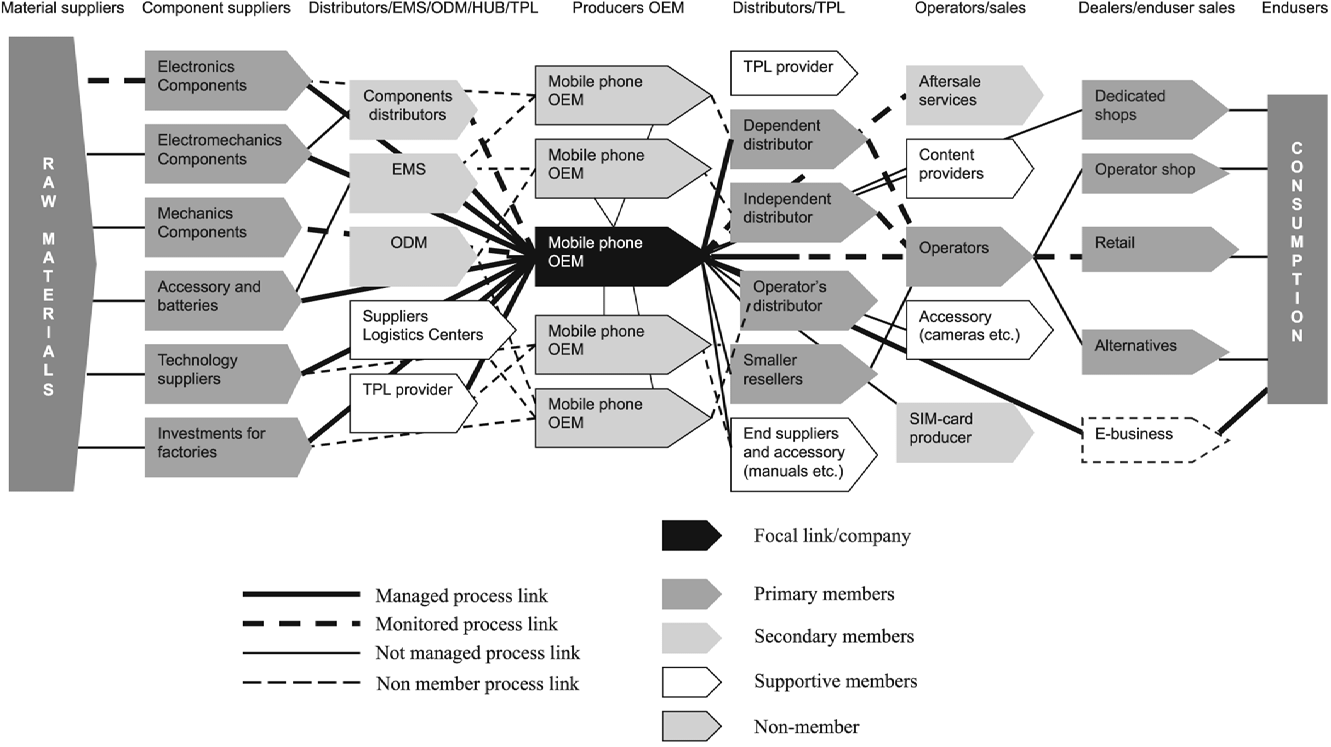
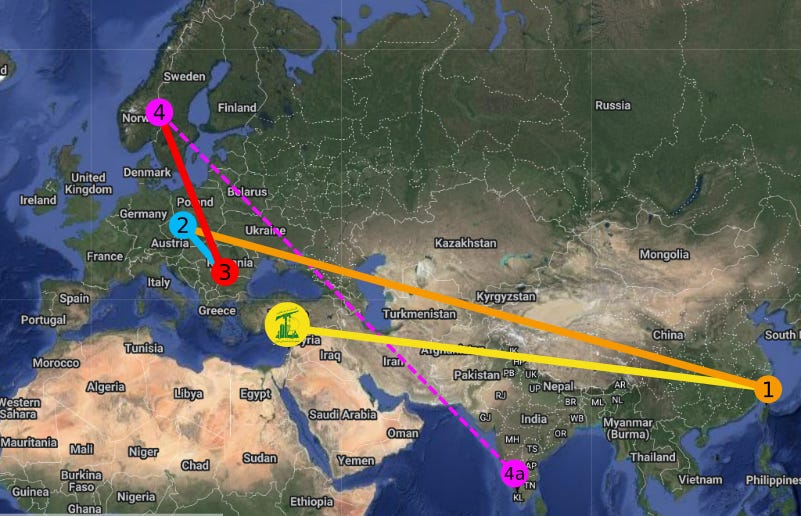
❶ Gold Apollo Company, Ltd.
One transaction node that has not been disputed by any party is also the first node. At some as-yet unidentified point in time, a representative of Hezbollah placed an order to Gold Apollo Co., Ltd. — a 30-year-old Taiwanese firm that specializes in pagers and walkie-talkies.
Publicly, Gold Apollo swears they were only a licensor, and points the finger of blame westward down the supply chain.
"The product was not ours. It was only that it had our brand on it," Gold Apollo founder and president, Hsu Ching-kuang, told reporters at the company's offices in the northern Taiwanese city of New Taipei on Wednesday.
The company said in a statement that the AR-924 model was produced and sold by BAC.
Gold Apollo authorised "BAC to use our brand trademark for product sales in specific regions, but the design and manufacturing of the products are entirely handled by BAC," the statement said.
“Design” you say? An exceptionally weird word to use here, even for a bunch of inscrutable Chinese Republicans. What do they mean when they claim they didn’t design the products? What’s this video about, then?
(Excerpts from a CommonWealth Magazine article by Lai Jianyu, 7/27/2011 (translation by Google Translate). Emphasis mine)
Golden Apollo sells walkie-talkies that are almost extinct in Taiwan, but its professional technology, customization and strict quality control have helped it win orders from European and American governments, ranking first in the United States and second in Europe.
Pagers and walkie-talkies have not been seen by many people for a long time. They were products that were eliminated several generations ago. Many major manufacturers have even listed them as antiques and put them in exhibition rooms. However, there are manufacturers in Taiwan that continue to work intensively, making the pager number one in the United States and second in Europe. Even the FBI is its customer, and its gross profit margin is not inferior to that of HTC and MediaTek.
Xu Qingguang, who originally specialized in the domestic market, discovered the demand in foreign markets when he went to participate in overseas exhibitions and found niche products purchased by foreign governments.
In fact, Golden Apollo's market development is almost entirely through cooperation with overseas agents, and it has repeatedly won cases from the FBI in the United States and fire bureaus in European countries.
By “cases” and “fire”, I’m sure our Engrish friend meant “contracts” and “five”. And if it’s not abundantly clear, the by-then obsolete pager and walkie-talkie company found a lucrative second life in the 2010’s, catering almost exclusively to the Intel Blob and its enforcement organs across the puppet empire.
In addition to outsourcing production and assembly, Golden Apollo is responsible for receiving orders, designing, purchasing raw materials, and then conducting quality control and shipping.
Considering the state of the rare earths markets (hint: picture the state of the board on your second-to-last turn of Monopoly), I can well imagine that the access to raw materials still counts for a lot. But as far as “designing“ these fucking things, any idiot can do that. Even with the native encryption and razzamatazz, you’re still basically just modding a beeper (or a two-way radio transceiver, in the case of walkie-talkies). But again: it’s not the tech itself these “overseas agents” are interested in. As usual, their key interests lie in covering their tracks and muddying the waters of accountability.
Here’s a link to their 9/18 announcement. Given that Gold Apollo has been transparent about their agency connections in the past, I don’t really see any reason to doubt them here. So let’s follow their gilded, deific, damning finger to the next (so far) undisputed node on the chain.
❷ BAC Consulting KFT
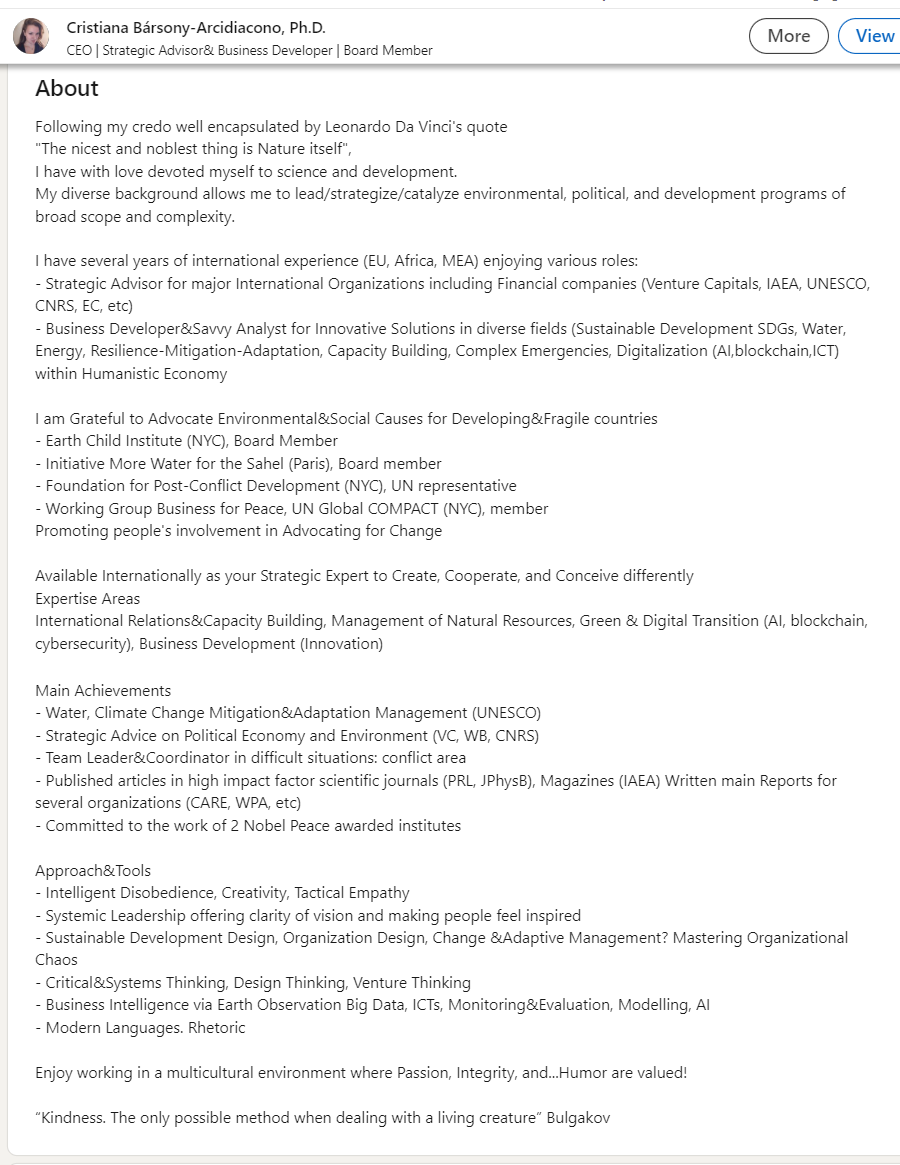
This two-year-old, Hungary-based business consulting firm is apparently managed and executed by a UK-educated Italian STEM genius, Green SlayQueen, cybersecurity expert, and “Venture Thinking” entrepreneur named Cristiana Barsony-Arcidiacono.
I went to the trouble of quickly screencapping her LinkedIn “About” page before it got scrubbed. See if anything stands out for you about the CV of Barsony-Arcidiacono (which literally translates to Velvet-Snob, by the way). I know I spied a few eyepoppers amid these now-deleted bullet points.
Wow! And bookended by quotes from Da Vinci and Bulgakov. A velvety bit of snobbery indeed.
Anyhow, despite BAC boasting the typical consultancy’s list of a gazillion-and-one services, there appears to be no evidence of any concrete means of production (manufacturing plants, warehouses, distribution centers, etc). In fact, so far BAC’s lone verified physical asset is its “corporate headquarters” — which appears to be a modest two-story apartment house in suburban Budapest.
This data point obviously raises suspicions about BAC’s true business model, as it seems to have “shell company” scrawled all over it in neon graffiti. But — superficially, at least — Christfollower Velvet-Snob’s protest that she was merely an “intermediary” in the pager transaction might pass the smell test (depending on what kind of crime you’re sniffing for, that is). Unfortunately, she likely won’t be shedding additional light on the subject any time soon:
Beatrix Bársony-Arcidiacono said by phone from Sicily that her daughter, Cristiana Bársony-Arcidiacono, “is currently in a safe place protected by the Hungarian secret services” after her Budapest-based company was linked to the devices used in the simultaneous pager attack on Tuesday.
But so far, Gold Apollo is a named node and BAC is a named node, and they both have seemingly acknowledged each others chain positions as 1 and 2, respectively.
Who else do we see in floating around in our narrative swamp?
❸ Norta Global Ltd
A potential third node comes in the form of a Bulgarian firm named Norta Global Ltd, which has yet to see much ink spilled outside of local finger-pointing and official denials.
The rumor was that we might find our missing factory (or at least an address for it) thereabouts. However, a preliminary look suggests yet another shell like BAC. No evidence of any relationship with manufacturing, shipping, or physical assets of any kind. And, of course, the company’s website has already been deleted.
The only listed physical location was an apartment building in Sofia, which also happened to be the directory listing for a couple of hundred other registered businesses. So, once more the only factory in sight is a paper(less) factory for (virtual)mailbox corporations.

While it’s proven difficult to validate (as usual), it’s now being reported that Norta Global received payments totaling 18 million krone (1.7 million USD) from an Israeli bank account over a two-year period. Seemingly reversing the transaction flow, this money was supposedly then redirected to BAC.
Unfortunately, the person who could most likely explain these ephemeral transactions is… also unavailable for comment.
❹ DN Media Group / Rinson Jose
Norta's Oslo-based founder of record is apparently some workaday slob named Rinson Jose, who has so far declined to comment on either the pager sales or the attack. Since I assume Jose’s LinkedIn will soon join Velvet-Snob in the abyss, I’ve once again screencapped his resume for posterity:
It’s perhaps an artifact of progressive Euro-suicidalism that the India born-and-educated Jose is described everywhere in their media as “Norwegian”. But apart from this tragicomic detail, there’s still no means of production or shipping to be found. Ironically, our trail runs cold in Norway, with a brown-faced Great Replacer from the sweltering subcontinent.
Or maybe it “runs cold” somewhere in the borderless hinterlands of what used to be the USA.
Norwegian police have issued an international search request for Rinson Jose, a Norwegian-Indian man linked to the sale of pagers to the Iran-backed Hezbollah terror group that exploded last week, they said on Thursday.
Jose, 39, disappeared while on a work trip to the US last week. He is a founder of a Bulgarian company that was reportedly part of the pager supply chain.
Asked what they were doing to find Jose, police said in an email to Reuters: “Yesterday, September 25, the Oslo police district received a missing person report in connection with the pager case.”
“A missing persons case has been opened, and we have sent out an international warrant for the person,” it added.
The case could even be made that the trail technically dead-ends in Hungary with BAC. If Velvet-Snob’s role as intermediary were to launder the next transaction node through an unwitting front (Rinson/Norta), then she may hold the key to the entire mystery.
So, at best, we have four “known” transactions, starting with the Hezbollah’s initial purchase order to Taiwan and ending at a middle class Dravidian immigrant’s ice hole in suburban Oslo, with nary a manufacturing node or transport record in sight. Just a bunch of disposable paper companies with evaporating CEOs and missing persons reports. There’s something to be said for the elegance of such disappearing acts, regardless of the magician’s morality and motives.
In its wake, we are left with a pile of unasked and unanswered questions.
How many manufacturing and shipping nodes are we even talking about, with regards to the components and subcomponents that go into the production of AR-924s? Are the devices made to order, or are completed assemblies sitting in warehouses, collecting dust until the call comes in?
How and when were they shipped, and by whom? How many ports of call? Why would Hezbollah name-drop Gold Apollo, but not the shipping personnel responsible for securing and delivering the shipment?
Who placed the order to Taiwan, and who or what prompted this choice of vendor? Why was Hezbollah allowed to screw up this badly on their own? Or were they? With an operation this mission critical, how could the Iranian intel services possibly be left out of the loop? Why wouldn’t they at least transact through a friendly nation instead of Western-aligned Taiwan? Did they get a deal on volume?
I have some questions about technical competency, too. I suppose it’s possible that neither Hezbollah nor their Iranian benefactors have anyone capable of reverse engineering a pager sufficiently to detect tampering. On the other hand — given the dark business they’re in — it beggars belief that PETN detection hadn’t crossed their minds. Even if they had to withhold a random sampling of pagers from personnel (say 10-15%, to be on the safe side) dismantle them completely, and feed each morsel through hardcore fluorescent chemosensors, it would be more than worth the trouble to do so. The proof is in the pudding.
But even leaving the explosive element aside, how would they validate that the devices weren’t bugged, or twigged in some other way? They’d still have to pop a few of those suckers open, and have them inspected by someone who knows what they’re looking at, yes? At the very least, you’d think they’d have some Persian connections that could vet such vital tools, or monitor the shipment’s journey through various ports of call. Does Hezbollah just blindly trust every sanctions-defying rocket that rolls off the back of a truck? Would they trust it the same if it had “Made in Taiwan” (or Bulgaria, or Hungary, or Norway) stamped on the side?
As for the breadcrumbs we’ve been fed, I’m not impressed. For all we know, all these various licensors, process outsourcers, mailbox companies, and shell corporations are just blind functionaries who don’t know or care how the magic beans are made.
As magic bean consumers, Hezbollah was also running blind and careless. Like the rebel rabble from my unpublished book, they thought they were strategically nerfing their tools. But a tool that you can’t make, repair or maintain yourself doesn’t fully belong to you. Or at least, not for long, if you forget your position on the chain.
For instance, you do not “own” your smartphone in the same way you might own a record collection, or the clothes on your back. Rather, the aspects of your phone that you do own3 are vastly outweighed by those you don’t. It would be akin to owning every part of your bicycle except the wheels, which Big Wheel can legally strip you of at any moment.
That goes triple for Network-based tools. In many cases, you literally (i.e. legally) do not own the most important aspects of those items. To be fair, an occupational paramilitary gang wouldn’t be too concerned about getting hauled into court by Motorola for fucking around with firmware. But if you can’t even do that, you have no business conducting an organization-wide rollout of their products. While pagers might seem “old fashioned” compared to the new cellular standard, the personnel they were issued to might as well be cavemen wielding ray-guns (and pointing them in the wrong direction to boot).
If it seems like I’m being “too hard” on Hezbollah, here, just have a quick look around your home or office. Take a moment to extrapolate the long, multi-threaded chains that produced all the magic beans you count.
How many of them receive signals from the ether?
If a bean makes it all the way to your doorstep, how can you possibly know what will sprout from it, one sunny day?
Which entity along that chain of ghostly nodes do you trust enough to deliver a product that isn’t ticking?
New Jack City
Just to be clear, I believe what transpired on the streets of Lebanon is at least an order of magnitude more dangerous than the nuclear arms race. As I mentioned in Magic Rules Iron:
The atomic magicians continued to pursue that shadowy line throughout the Cold War. But as per usual, the rule of magic didn’t last very long. That’s because the instant someone else gains access to your doomsday device, that device no longer exists for all practical purposes. You can’t “end the world better” than the next guy.
That doesn’t mean the king abandons magic. For one thing, being an unimaginative dunderhead is a common trait of those who ascend the ladders of leadership these days. Hence the insanity of the arms race towards the end, when both sides kept churning out nukes well beyond any realistic advantage it would yield them. And once India and China had the tech, that was all she wrote. It was a dragon that blows up the wizard's own castle when he summons it, so no wizard ever would.
We were all raised under the specter of global thermonuclear warfare. But as one weird consequence of that, the whole idea became blasé, and particularly for Generation X. There were no “duck and cover drills” for us, or backyard shelters loaded up with canned goods. It was instead ingrained in us that, should such a doomsday ever arrived, there would be literally nothing we could do about it.
But the specter that looms over Internet of Things isn’t so kind to the 21st century psyche. For one thing, it dangles the remote-yet-plausible chance that we actually can do something about it, if we just take the proper precautions.
There are certainly products one could buy and lifestyle adjustments one could make that will marginally reduce the risk of, say, getting blown to flaming briskets by your Alexa. But the truth is that nothing short of living fully off-grid in the wilderness is going to significantly improve your armor rating. Not in the current environment, at least.
Much of the reason has to do with the way our global supply chain works. The paradox of our age is that essentially every product we buy has, at some point in the process, passed through the hands of an “enemy” who wouldn’t mind very much if you were maimed or poisoned or dead. That’s as true for a resident of Beirut as it is for one of New York City, or Paris, or St. Petersburg, or even Beijing.
Therefore, anyone who claims that international trust is in short supply is either blissfully ignorant, or trying to sell you a bridge in Brooklyn. Every waking moment is an act of trust that the products and services we use won’t harm us. If anything, the citizens of every nation have become altogether too trusting of vertical integration and the producer-consumer economy, lulled into a false sense of security by the dopamine hits.
This spell of trust has spread so far and wide, even organizations that are paranoid-by-design seem to have fallen under it. When Nasrallah named the “agent” as “the phone in your hands” he condemned his loyal soldiers to a half-truth. He pointed at the tail instead of the dog, yet somehow still trusted the invisible giant holding its leash in the clouds.
I made the same childish error, about a decade ago. A sweet summer child, ignorant to the thunderbolt-shitting elephant in the room. I even initially mistook Hezbollah for the canary in the coalmine, when the fact was similar birds have been shrieking their little heads off for more than a generation now. We were all born and raised as cargo cultists, and we’re on the verge of finding out exactly what happens when those planes stop landing.
Meanwhile a fellow named Harold J. Daggett — President of the International Longshoreman’s Association, a guy who probably couldn’t tell firmware from tupperware — lays it out as plain as Ozymandias in his prime:
“You know what’s gonna happen? I will tell you. First week, be all over the news every night. Boom, boom. Second week, guys who sell cars can’t sell because they’re coming in off their ships. They get laid off. Third week, malls start closing down. They can’t get goods from China. They can’t sell clothes. Thy can’t do this. Everything in the United States comes on a ship. They go out of business. Construction workers get laid off because their materials aren’t coming in. The steel’s not coming. The lumber is not in. They lose their job.
He goes on to say what everyone who’s ever experienced a “work slowdown” of critical services already knows. At the end of the day, they hold all the cards. It doesn’t matter what elected officials and staffers and pundits say, or even what those invisible “unnamed military and intelligence sources” say. Thanks to decades of deindustrialization, outsourcing, offshoring, and the insanity of the globocap telos, and we are all in cargo cult now.
That may sound just fine and dandy to a guy like Uncle Ted. But for the rest of us, it means the supply lines for our most powerful tools of communication and organized resistance have been totally compromised. The Daggetts of the world may think themselves invincible — and maybe, for the moment they are. But get ready for the mother-of-all reactions from the Blob. I wouldn’t be surprised if I find myself scabbing at some shipyard before year’s end, fending off stevedores with improvised weapons.
If the Enemy wins this round, we’ll be plunged into an even deeper level of doo-doo. The elites will use this and all other recent supply chain attacks as fig leaf, to further degrade our ability to buy, use, sell, and modify any technology that could potentially be used to oppose them (and be on the lookout for a copycat attack against Western populations as well, just to seal the deal).
So unless we plan to fight World War Weird with literal slings and arrows, and coordinate our action by birdcalls and smoke signals, we’ll need to map out some workarounds, fast. Our solutions need to be mobile, robust, and non-reliant on international bean supplies for initial rollout and upkeep.
This will naturally include the establishment of small-n comms-networks that can be independently secured, controlled, maintained, defended, and — if necessary — dissolved at a moment’s notice, if the shit hits the fan. If Punjabi IT Vikings and Velvet UNESCO Snobs can it pull off, imagine what our growing meta-nation of polymathic rebels might accomplish at a fraction of the price?
I have a few ideas. For my unpublished book, that is. Purely in the realm of science fiction fairy tales.
Perhaps a few of you out there also have an interest in science fiction, or fairy tales.
If so, let’s discuss some art, shall we?
(To get your creative juices flowing, here’s some food for thought)
The Cat Was Never Found is a reader-supported blog. I don’t publish much paywalled content, so your generous patronage is very much appreciated. As a reminder, a paid subscription will also grant you access to Deimos Station; the happiest place in cyberspace!
P.S. If you found any of this valuable (and can spare any change), consider dropping a tip in the cup for ya boy. It will also grant you access to my “Posts” section on the donation site, which includes some special paywalled Substack content. Thanks in advance.
Mossad agents almost certainly among them (but also almost certainly not the sole culprits involved).









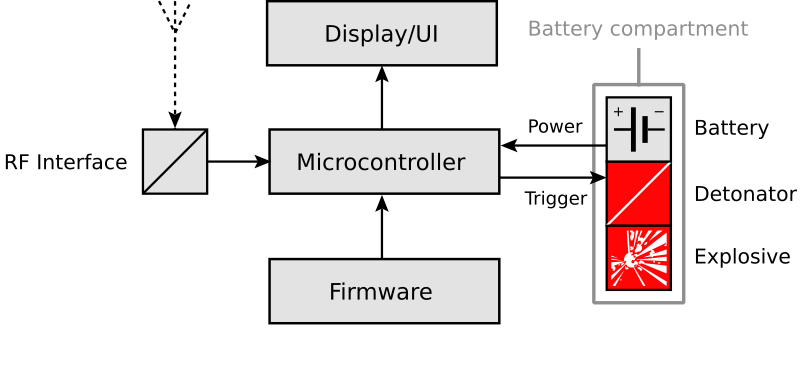







It occurred to me as I read this that a nation-state terrorist setting up this attack would simply include the explosive in the molding process for the case. Many forms of RDX can only be detonated by electricity, resisting even small arms fire, and could be overmolded leaving virtually no trace. All that is required then would be a custom PCB with traces in the right place and a custom firmware. I suspect that Mossad or their affiliates could do this where it would be very nearly untraceable.
To me though the key to the whole attack is how they knew that this purchase was from Hezbollah. I suspect that there are enough large corporate clients making similar purchases that this simply isn't possible without an inside man in Hezbollah's procurement.
The fact that this is an actual attack is what makes it stand out the most. What I mean is that most attacks between nominal enemies is deliberately nerfed ahead of time. For example, before Iran's recent penetration of the Iron Dome they called Israel to make sure that all of their planes were in the air and wouldn't be hit, a move that I still find bizarre.
Other than that all I can say is, Why run your mouth about Bruce Campbell? He may be the closest thing to a living hero that we have left. Ash knew to fight demons not make deals with them and when his hand tempted him to sin he cut it off. His old school loyalty and competence made Burn Notice.
An epic piece of writing! Thank you!